Day 14 网页分析 - Web Application Analysis (wpscan - WordPress vulnerability scanner)
前言
又进到一个新的分类Web Application Analysis,顾名思义就知道要来分析网站的弱点了,今天要介绍的工具是wpscan,是一个WordPress vulnerability scanner,非常有针对性的一个工具,所以在开始介绍之前有必要先提一下什麽是WordPress。
什麽是WordPress
有架站需求的朋友应该都有听过这个名字,WordPress是一个非常热门的网页制作平台、网站管理系统。根据w3techs的统计,市占率截至今年八月已经成长到42.6%。然而WordPress还细分成WordPress.com以及WordPress.org,前者是一个网页制作平台,在上面可以套用大量的布景主题、外挂,能满足各种网页需求,像是架设个人部落格、品牌网站等等,但也有种种限制来自平台方,很难达到较细部的客制需求;而後者WordPress.org是一套软件,让我们可以快速在主机上架设起网站,同样也能套用各种资源,但不同的是,这些资源包含程序码都能修改,所以也更适合有程序基础的人。
工具介绍
不管透过官方平台或是自己架设的WordPress网站,就都是这次介绍的工具wpscan锁定的目标了,它位於Kali的Web Application Analysis分类之中,直接执行可以看到介绍与基本用法
Executing “wpscan --help”
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
Usage: wpscan [options]
--url URL The URL of the blog to scan
Allowed Protocols: http, https
Default Protocol if none provided: http
使用方法很简单,输入目标机就好,这边我们用之前Day2建立的靶机来测试
wpscan --url http://192.168.1.86
结果很快出来了...什麽都没有
Scan Aborted: The remote website is up, but does not seem to be running WordPress.
尴尬了,因为靶机上根本不是属於WordPress体系的网站,但又不能去找线上网站来测试,所以只好自己架一个了。
架设WordPress网站
因为我们要自己在机器上架设网站,所以不会是去WordPress.com,而是到WordPress.org下载页面找寻适合的版本。因为目的是想体验扫描工具,所以这里我选择了一个比较旧的版本wordpress-4.7-RC1.tar.gz,预期是直接安装在Day2介绍的靶机上。
- 先
ssh进入到靶机,下载档案并解开
# 下载档案
wget --no-check-certificate https://wordpress.org/wordpress-4.7-RC1.tar.gz
# 解压缩
tar xvf wordpress-4.7-RC1.tar.gz
- 因为之後wordpress的设定会需要设定mysql,所以先在这里准备好
# 以root登入,密码预设是空的,直接enter就能进入mysql shell
mysql -uroot -p
进到mysql後,新建一张名叫wordpress的表後离开
mysql>CREATE DATABASE wordpress;
mysql>exit;
- 将靶机当前的apache停掉
# 关闭apache2
sudo /etc/init.d/apache2 stop
# 备份原本的www资料夹,这是原本apache2运行的网站根目录
sudo mv /var/www /var/www.bak
# 建立软连结,将步骤1下载解开的资料夹指到apache2根目录
ln -s /home/msfadmin/wordpress /var/www
# 重新启动apache2
sudo /etd/init.d/apache2 start
- 开启浏览器前往靶机网页页面
当apache2重新开始运行,这样透过靶机http://192.168.1.86就能看到wordpress的初始页面
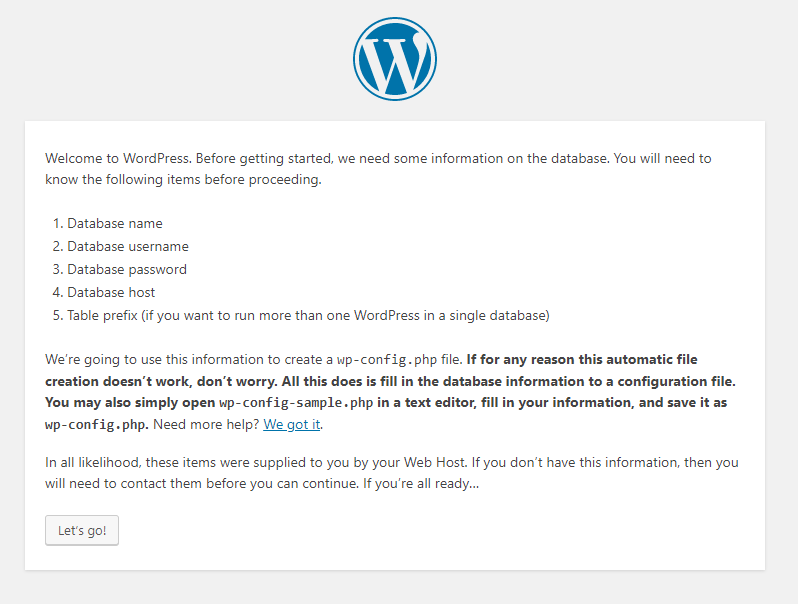
显然还需要经过设定才能把网站架起来,所以点击按钮继续後续设定。这边根据前面mysql设定即可,如果跟我一样用靶机,那这边就跟着图修改Username为root、Password留白即可。
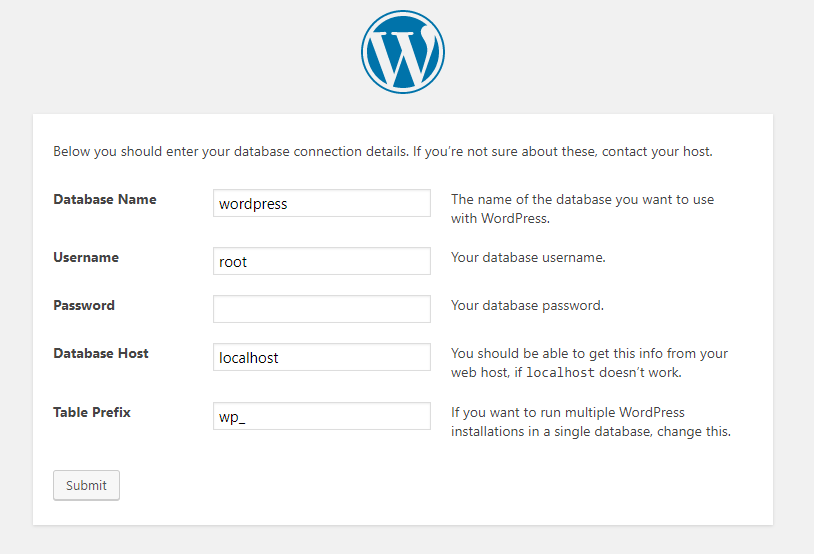
接着可能会因为软件无法写入设定档,所以会要求自行编辑档案。
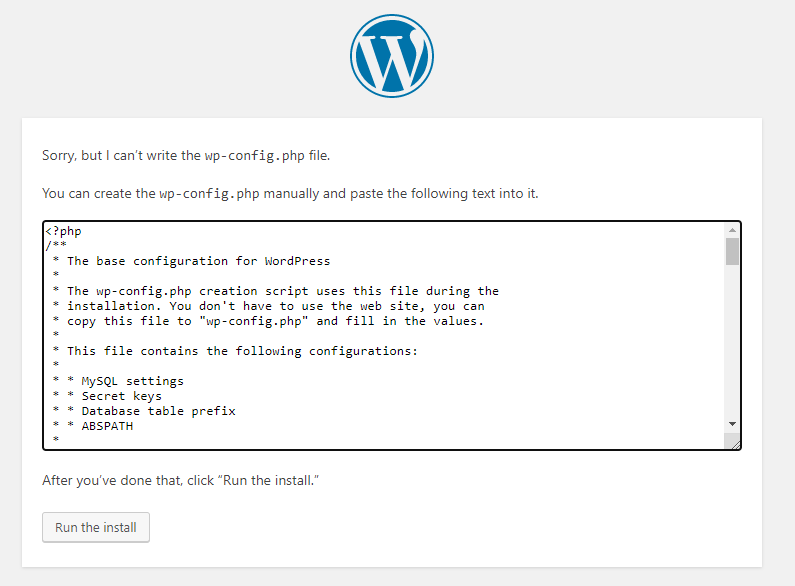
# 先进到 /var/www (记得这边已经指到/home/msfadmin/wordpress)
cd /var/www
# 透过 vi 或其他编辑器,将网页上显示的内容复制到档案里
vi wp-config.php
自行编辑wp-config.php後才能继续下一步,这边就填入一些基本资讯就可以了。
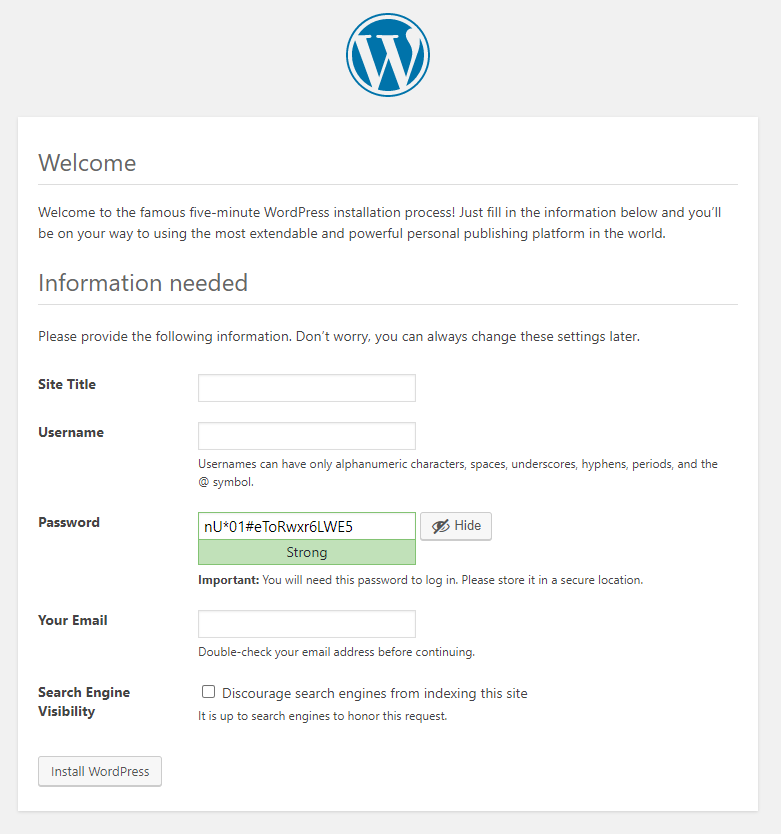
看到这页就表示网站已经设定完成,所有的一切都是预设样式,但这并不妨碍我们测试。
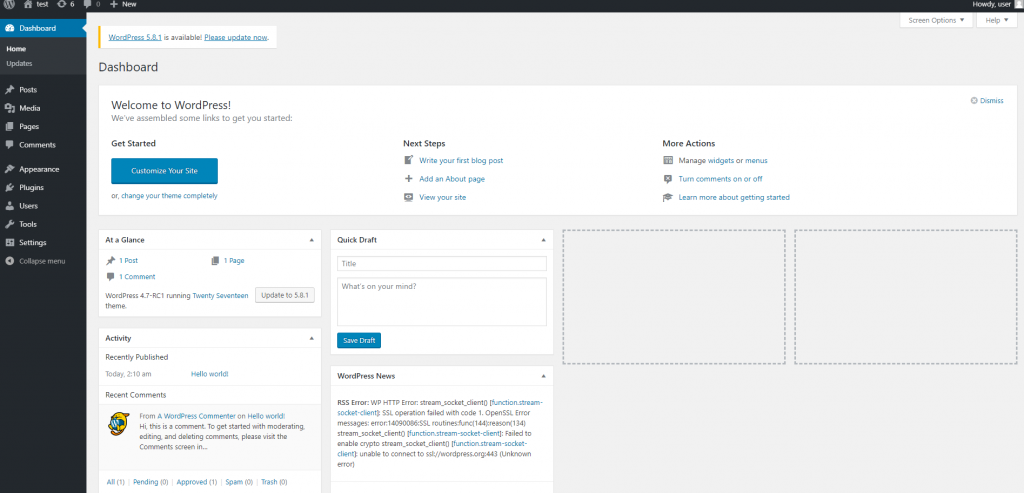
再次使用wpscan
经过前面一连串步骤,我们终於有了自己的WordPress网站可自由测试了,所以事不宜迟马上开打,别忘了这里我们回到Kali使用wpscan来测试目标靶机,不是在靶机上继续操作罗。
# 192.168.1.86是我的靶机IP
wpscan --url http://192.168.1.86
这次就有侦测结果了。
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.17
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://192.168.1.86/ [192.168.1.86]
[+] Started: Wed Sep 29 09:52:00 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: Apache/2.2.8 (Ubuntu) DAV/2
| - X-Powered-By: PHP/5.2.4-2ubuntu5.10
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://192.168.1.86/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://192.168.1.86/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://192.168.1.86/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.7 identified (Insecure, released on 2016-12-06).
| Found By: Emoji Settings (Passive Detection)
| - http://192.168.1.86/, Match: 'wp-includes\/js\/wp-emoji-release.min.js?ver=4.7'
| Confirmed By: Meta Generator (Passive Detection)
| - http://192.168.1.86/, Match: 'WordPress 4.7'
[+] WordPress theme in use: twentyseventeen
| Location: http://192.168.1.86/wp-content/themes/twentyseventeen/
| Last Updated: 2021-07-22T00:00:00.000Z
| Readme: http://192.168.1.86/wp-content/themes/twentyseventeen/README.txt
| [!] The version is out of date, the latest version is 2.8
| Style URL: http://192.168.1.86/wp-content/themes/twentyseventeen/style.css?ver=4.7-RC1
| Style Name: Twenty Seventeen
| Style URI: https://wordpress.org/themes/twentyseventeen/
| Description: Twenty Seventeen brings your site to life with immersive featured images and subtle animations. With...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://192.168.1.86/wp-content/themes/twentyseventeen/style.css?ver=4.7-RC1, Match: 'Version: 1.0'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:00 <> (105 / 137) 76.64% ETA: 00:00:0 Checking Config Backups - Time: 00:00:00 <> (110 / 137) 80.29% ETA: 00:00:0 Checking Config Backups - Time: 00:00:00 <> (117 / 137) 85.40% ETA: 00:00:0 Checking Config Backups - Time: 00:00:00 <> (124 / 137) 90.51% ETA: 00:00:0 Checking Config Backups - Time: 00:00:00 <> (132 / 137) 96.35% ETA: 00:00:0 Checking Config Backups - Time: 00:00:00 <> (136 / 137) 99.27% ETA: 00:00:0 Checking Config Backups - Time: 00:00:01 <> (137 / 137) 100.00% Time: 00:00:01
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Wed Sep 29 09:52:12 2021
[+] Requests Done: 172
[+] Cached Requests: 5
[+] Data Sent: 42.513 KB
[+] Data Received: 347.278 KB
[+] Memory used: 232.383 MB
[+] Elapsed time: 00:00:12
结语
今天我们实际体验了如何架设烂网站,透过自己架设的简易WordPress网站,来体验wpscan这套工具的使用方法。虽然目前我手边并没有实际在管理WordPress网站,但也许未来会需要也说不定。但其实也更好奇,目前网站架设生态系这麽复杂,各种框架像是神仙大乱斗,是否都有其针对性的扫描工具呢?
# Day14--解决暧昧问题延伸出来的那些事
前言 可选在上一篇中,提到一个概念就是暧昧。它是一种可以让程序介於「有值」、「没有值」的中间状态,这...
Day12 咸香下饭好帮手-金银蛋炒四季豆
上次有小夥伴说苍蝇头的菜菜太少,肉末比菜菜多,这次改进,推出另外一道咸香下饭的菜菜料理- 金银蛋炒四...
Day15:今天来聊一下Microsoft Defender for Endpoint的威胁分析
随着敌人越来越复杂、新威胁频繁出现且越来越普遍,一定要能快速完成以下工作: -评估新威胁的影响 -检...
3 所以要长怎样?
聊一下更新画面这回事 自己以前的经验,我在出一张牌的时候,都是从前端通知後端说出了牌,更新完服务器端...
Leetcode: 112. Path Sum
问你这棵树有没有哪条从root到leaf的路径,是满足路径上的节点加总起来等於targetsum的?...